Install and Configure Squid Proxy in Ubuntu
Squid is a full-featured web proxy cache server application that provides proxy and cache services for HTTP, FTP, and other popular network protocols that you can easily install in Ubuntu.
This guide will show you how to create your own HTTP proxy using Squid, a highly customizable proxy/cache application, in Ubuntu 18.04 VM Instance in ServerStadium.
An HTTP proxy acts as an intermediary between you and the internet. While connected to your Squid HTTP proxy, you will be able to:
- Anonymously access internet services.
- Bypass certain regional and local network restrictions.
Installing Squid
First, make sure the server is up to date by running the following commands as sudo user:
$ sudo apt update && sudo apt upgradeAfter you ensure your system is up to date, continue with the Squid Installation.
$ sudo apt install squidThen check the installation by using the following command; if the installation succeeded, it will produce this following output:
$ sudo systemctl status squid
Output:
● squid.service - LSB: Squid HTTP Proxy version 3.x
Loaded: loaded (/etc/init.d/squid; generated)
Active: active (running) since Thu 2020-09-17 12:06:07 UTC; 4min 46s ago
Docs: man:systemd-sysv-generator(8)
.....
Configuring Firewalls
We should ensure that our Ubuntu VM Instance Squid Port (TCP Port 3128) is not blocked by ServerStadium Security Profile and UFW Firewall.
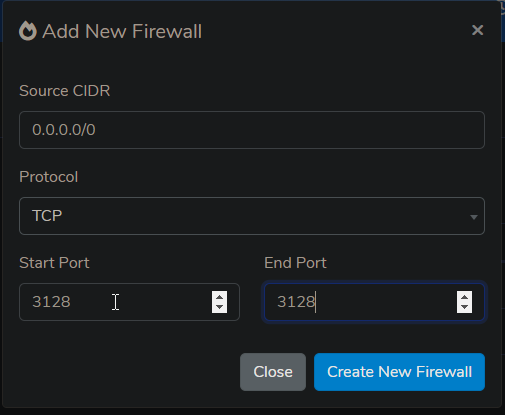
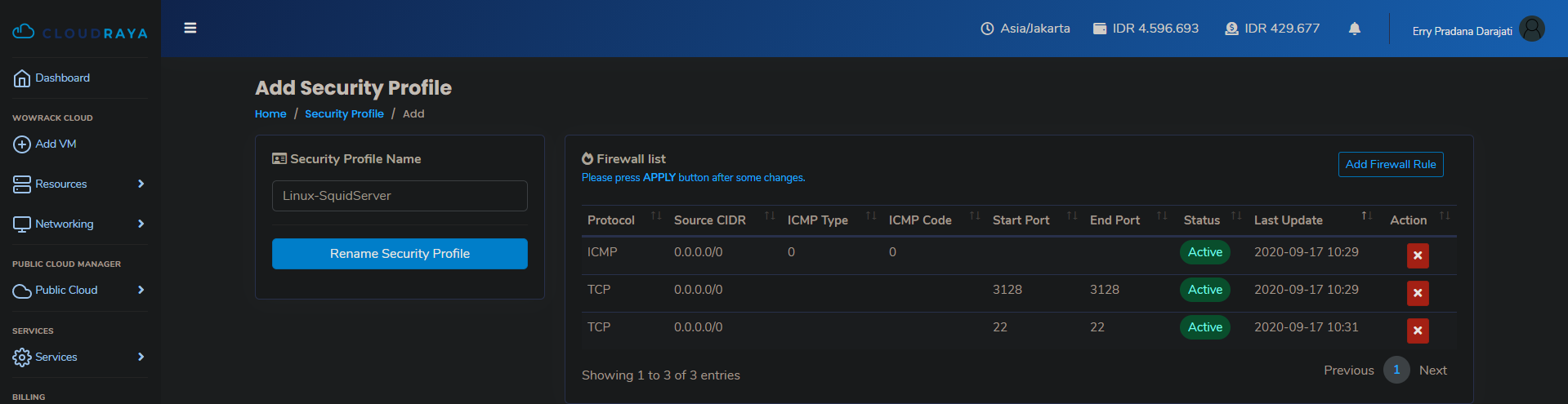
To modify ServerStadium Cloud Security Profile, open the ServerStadium Cloud panel and navigate to Networking Sidemenu -> Security Profile. Then, edit or create a new Security Profile.
Add a new Firewall Rule on the Security Profile page that opens TCP port 3128. Then apply the security profile.
We also need to ensure Inbound TCP port is allowed in Ubuntu UFW. To do this, run the following command in the Ubuntu VM we installed with Squid server.
$ sudo ufw allow 'Squid'To verify the firewall status, type the following command and the output will be shown below
$ sudo ufw status
Output:
Status: active
To Action From
-- ------ ----
OpenSSH ALLOW Anywhere
Squid ALLOW Anywhere
OpenSSH (v6) ALLOW Anywhere (v6)
Squid (v6) ALLOW Anywhere (v6)
Configuring Squid
Now that Squid is installed on our ServerStadium Cloud Ubuntu VM, we can configure it to accept connections and serve as an HTTP proxy.
Squid can be configured by editing the /etc/squid/squid.conf file. You can also use separate files with configuration options which can be included using the “include” directive.
The configuration file contains comments that describe what each configuration option does.
Before making any changes, it is a good practice to back up the original configuration file by running the following commands:
$ sudo cp /etc/squid/squid.conf{,.orginal}Edit the file by opening it using nano (or another text editor):
$ sudo nano /etc/squid/squid.conf
Configuring Client Access via IP ACL
In Squid, you can control how the clients can access the web resources using the Access Control Lists (ACLs).
By default, Squid allows access only from the localhost.
If all the clients using the proxy have a static IP address, you can create an ACL that includes the allowed IPs.
Instead of adding the IP addresses in the main configuration file, we will create a new dedicated file that will hold the IPs:
$ sudo nano /etc/squid/allowSourceIP.txt
192.168.33.1
# All other allowed IPsOnce done, open the main configuration file and create a new ACL named allowSourceIP (first highlighted line) and allow access to that ACL using the http_access directive (second highlighted line):
# ...
acl allowSourceIP src "/etc/squid/allowSourceIP.txt"
http_access allow localhost
#Allow access from localhost
http_access allow allowSourceIP #Allow access from IP List
# And finally deny all other access to this proxy
http_access deny allThe http_access directive works similarly to the firewall rules. Squid reads the rules from top to bottom, and when a rule matches, the rules below are not processed.
Since the order of http_access rules are important. Make sure you add the line before http_access deny all.
Please keep mindful that whenever you make changes to the config file, you need to restart the Squid service with the following command:
$ sudo systemctl restart squid
Configuring Client Access via Basic Authentication
Besides limiting access via IP, we can also configure Squid HTTP proxy via basic HTTP authentication.
- Install htpasswd by installing the Apache utility programs. If you have installed Apache on your Cloudraya Ubuntu VM, you will already have it and can skip this step.
$ sudo apt-get install apache2-utils2. Create a file to store Squid users and passwords:
$ sudo touch /etc/squid/squid_usr3. Change ownership of the password file:
$ sudo chown proxy /etc/squid/squid_usr4. Check the location of the ncsa_auth file:
$ sudo dpkg -L squid | grep ncsa_auth5. Edit the Squid configuration file (/etc/squid/squid.conf) and add the following lines at the beginning of the file. Make sure that you update /usr/lib/squid/basic_ncsa_auth below with the location of the ncsa_auth file that you checked in the previous step:
auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/squid_passwd
acl ncsa_users proxy_auth REQUIRED
http_access allow ncsa_usersOnce you’ve saved and exited the file, complete user removal by restarting Squid:
$ sudo systemctl restart squid
Blocking access to restricted domain
One of the features of Squid proxy server is blocking websites for the client that connects to our Squid Proxy server. It can be done using forbidden dstdomain keyword in ACL directive.
First, we need to create the file. Then add domain names that we need to restrict:
$ sudo nano /etc/squid/forbidden_domains.txt
Contains:
.facebook.com
.twitter.com
.tiktok.comAfter we create the list of domains in a text file, we modify the Squid configuration file as follows:
# ...
acl allowSourceIP src "/etc/squid/allowSourceIP.txt"
#Add a new ACL directive
acl forbidden dstdomain "/etc/squid/forbidden_domains"
http_access allow localhost
#Allow access from localhost
http_access allow allowSourceIP #Allow access from IP List
#Add the restricted server in the deny list
http_access deny forbidden
# And finally deny all other access to this proxy
http_access deny allAfter that, don’t forget to restart the Squid service to apply the changes
$ sudo systemctl restart squid
Anonymizing Traffic
We also can anonymize clients that connect to our Squid proxy. Thus, IP address of the clients that connects to our Squid proxy will not be forwarded to servers that receive traffic from our Squid Proxy.
This is done via the rules below. Add the following lines at the beginning of the Squid configuration file:
forwarded_for off
request_header_access Allow allow all
request_header_access Authorization allow all
request_header_access WWW-Authenticate allow all
request_header_access Proxy-Authorization allow all
request_header_access Proxy-Authenticate allow all
request_header_access Cache-Control allow all
request_header_access Content-Encoding allow all
request_header_access Content-Length allow all
request_header_access Content-Type allow all
request_header_access Date allow all
request_header_access Expires allow all
request_header_access Host allow all
request_header_access If-Modified-Since allow all
request_header_access Last-Modified allow all
request_header_access Location allow all
request_header_access Pragma allow all
request_header_access Accept allow all
request_header_access Accept-Charset allow all
request_header_access Accept-Encoding allow all
request_header_access Accept-Language allow all
request_header_access Content-Language allow all
request_header_access Mime-Version allow all
request_header_access Retry-After allow all
request_header_access Title allow all
request_header_access Connection allow all
request_header_access Proxy-Connection allow all
request_header_access User-Agent allow all
request_header_access Cookie allow all
request_header_access All deny allAfter that, close the config file and restart your Squid proxy.
Connecting to your Squid Proxy
Your Squid Proxy Server is now ready, Congratulations!
You can configure your local browser or operating system’s network settings to use your ServerStadium VM as an HTTP proxy. The settings to do this will vary depending on your OS and browser.
You may find several official articles below to configure your Client OS or Browser to connect to the Squid Proxy:

